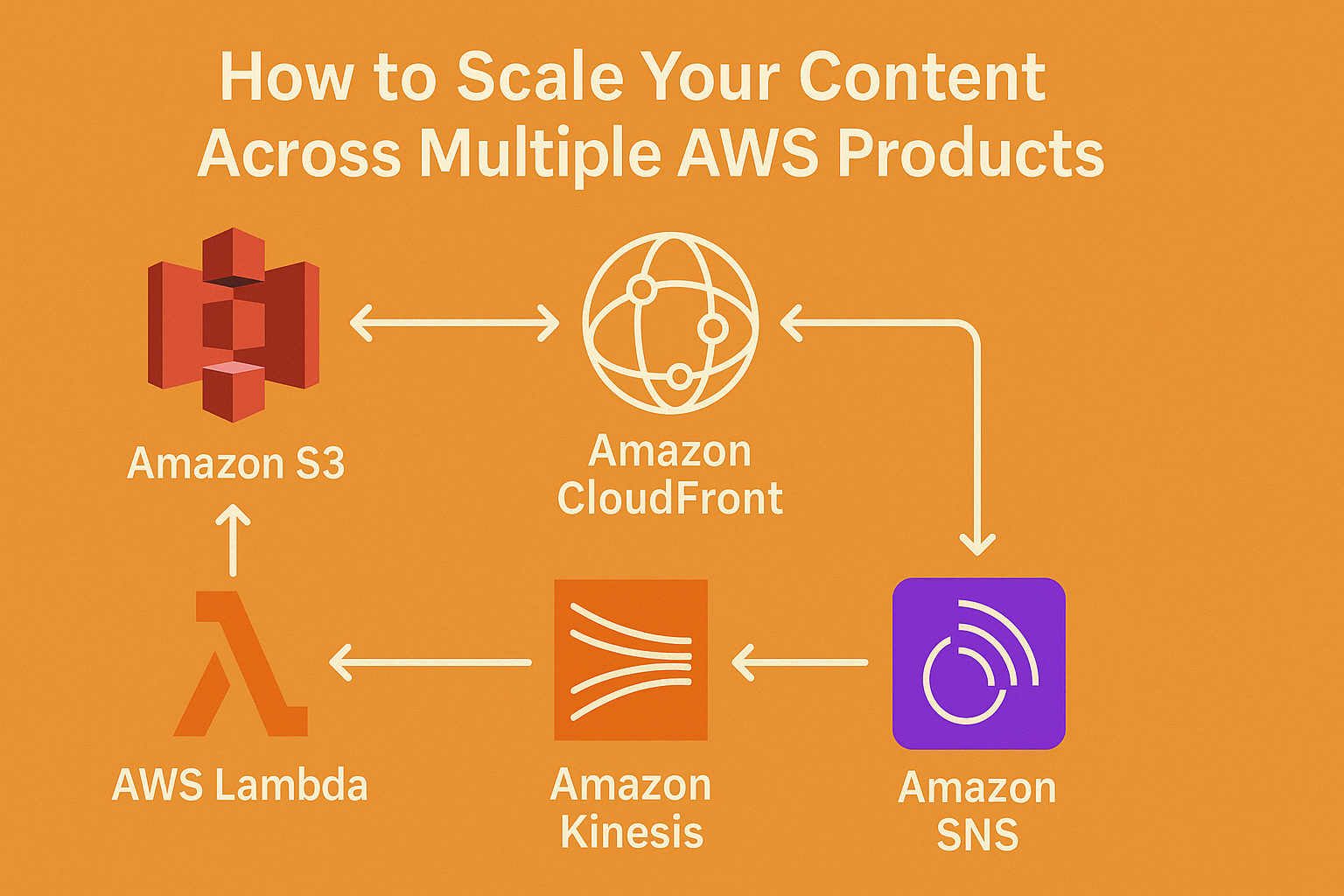
Introduction
Downtime is expensive. In a cloud-native environment, even a few minutes of service disruption can mean lost revenue, SLA breaches, and customer churn.
The good news? With the right mix of AWS automation services and AI-driven decision-making, you can build a self-healing architecture, one that detects failures, takes corrective action, and restores service without waiting for a human engineer.
This isn’t science fiction. AWS gives you the tools today.
Why Self-Healing Matters
Traditional incident response often looks like this:
- Monitoring system detects an anomaly.
- An alert is sent to on-call staff.
- The engineer investigates.
- A fix is applied manually.
The delays between detection and action add risk. A self-healing system shortens that gap to seconds.
Core Components of a Self-Healing AWS Setup
1. Detection Layer
- Use Amazon CloudWatch alarms, logs, and metrics.
- Add AWS X-Ray for tracing service-to-service performance issues.
2. Event Routing
- Feed alerts into EventBridge to trigger the healing workflow.
3. AI-Driven Diagnosis
- Lambda function calls an AI model (Amazon Bedrock or SageMaker) to:
- Classify incident type (network, compute, DB, app error).
- Recommend remediation action based on past incidents.
4. Automated Remediation Scripts
- Store pre-approved scripts in AWS Systems Manager (SSM) Automation:
- Restart EC2 instances or containers.
- Redeploy failed CodePipeline stages.
- Scale up services temporarily.
- Swap traffic to healthy endpoints with Route 53.
5. Post-Action Validation
- AI model re-checks logs/metrics to confirm the issue is resolved.
- If unresolved, escalate to human intervention.
Self-Healing Flow Example
Scenario: A production API hosted on ECS sees a sudden spike in 5xx errors.
- CloudWatch detects the spike.
- EventBridge routes the event to Lambda.
- AI model analyzes logs and past incidents—detects container crash loop.
- SSM Automation script triggers ECS task replacement.
- AI rechecks CloudWatch metrics to confirm error rate returns to baseline.
- Incident is marked “resolved” in ServiceNow or Jira without waking up the on-call engineer.
Best Practices for AI + Automation Healing
- Maintain a library of safe remediation scripts that can be run without approval.
- Log all AI decisions and remediation actions for compliance audits.
- Start in shadow mode, AI suggests actions, but humans approve, before going fully autonomous.
- Use tag-based targeting so scripts only run on relevant resources.
- Keep manual override paths for high-risk systems.
Benefits
| Benefit | Traditional Ops | AI + Self-Healing Ops |
|---|---|---|
| Detection to Action Time | Minutes to hours | Seconds to minutes |
| On-Call Fatigue | High | Reduced alerts to humans |
| SLA Compliance | Risk of breach | Higher uptime reliability |
| Ops Cost | Higher due to manual work | Lower through automation |
| Customer Trust | Reactive | Proactive, stable service |
Conclusion
A self-healing AWS architecture means your systems detect, diagnose, and resolve many issues without waiting for human intervention.
When you combine AWS native automation with AI-powered decision-making, you build a cloud environment that is:
- More resilient
- Faster to recover
- Cheaper to operate